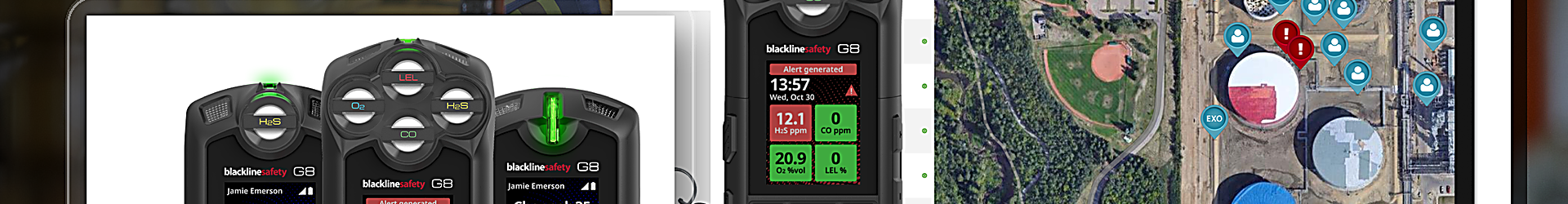
Listen to the article Data breaches and a demand for stricter security measures are inspiring companies to invest in obtaining a System and Organizational Controls (SOC) 2 report. Without one, businesses can lose deals or fail audits. Companies that work with a SOC 2 consulting partner improve their funding and […]